Insecure HTTP Method
- Risk:
Medium
- Type:
- Active
- CWE:
- CWE-200
- Summary
The most common methodology for attackers is to first footprint the target’s web presence and enumerate as much information as possible. With this information, the attacker may develop an accurate attack scenario, which will effectively exploit a vulnerability in the software type/version being utilized by the target host.Multi-tier fingerprinting is similar to its predecessor, TCP/IP Fingerprinting (with a scanner such as Nmap) except that it is focused on the Application Layer of the OSI model instead of the Transport Layer. The theory behind this fingerprinting is to create an accurate profile of the target’s platform, web application software technology, backend database version, configurations and possibly even their network architecture/topology.
- Solution
Implement measures to obfuscate or disguise information about the system's platform, web application software technology, backend database version, configurations, and network architecture/topology. This can include: 1. **Platform and Software Diversity:** Use a mix of technologies and platforms to make it harder for attackers to build an accurate profile. 2. **False Information:** Introduce fake or misleading information in system responses to confuse fingerprinting tools. 3. **Response Randomization:** Randomize certain elements in responses to make it difficult for attackers to consistently identify the system. 4. **Firewall Rules:** Implement firewall rules to block or limit the effectiveness of fingerprinting techniques. 5. **Regular Updates:** Keep software, platforms, and configurations up-to-date to patch known vulnerabilities and prevent accurate identification based on outdated information. There is no one-size-fits-all solution, and a combination of these measures may be most effective.
American Airlines subsidiary Envoy confirms Oracle data theft attack
Microsoft lifts more safeguard holds blocking Windows 11 updates
Europol dismantles SIM box operation renting numbers for cybercrime
Microsoft fixes Windows bug breaking localhost HTTP connections
North Korean Hackers Combine BeaverTail and OtterCookie into Advanced JS Malware
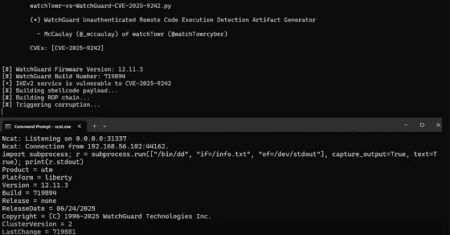
Researchers Uncover WatchGuard VPN Bug That Could Let Attackers Take Over Devices
CVE-2025-54253 Adobe Experience Manager Forms Code Execution Vulnerability
CVE-2016-7836 SKYSEA Client View Improper Authentication Vulnerability
CVE-2025-6264 Rapid7 Velociraptor Incorrect Default Permissions Vulnerability
CVE-2025-59230 Microsoft Windows Improper Access Control Vulnerability
CVE-2025-24990 Microsoft Windows Untrusted Pointer Dereference Vulnerability
CVE-2025-47827 IGEL OS Use of a Key Past its Expiration Date Vulnerability
CVE-2025-27915 Synacor Zimbra Collaboration Suite (ZCS) Cross-site Scripting Vulnerability
CVE-2025-61882 Oracle E-Business Suite Unspecified Vulnerability
CVE-2010-3765 Mozilla Multiple Products Remote Code Execution Vulnerability
Free online web security scanner