X-AspNet-Version Response Header
- Risk:
Low
- Type:
- Passive
- Summary
Server leaks information via “X-AspNet-Version”/“X-AspNetMvc-Version” HTTP response header field(s).
- Solution
Configure the server so it will not return those headers.
- Other info
- An attacker can use this information to exploit known vulnerabilities.
- References
https://www.troyhunt.com/shhh-dont-let-your-response-headers/
https://blogs.msdn.microsoft.com/varunm/2013/04/23/remove-unwanted-http-response-headers/
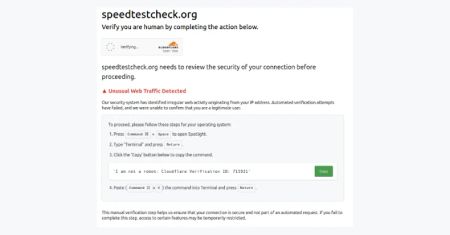
Hackers Exploit WordPress Sites to Power Next-Gen ClickFix Phishing Attacks
Hackers Exploit Milesight Routers to Send Phishing SMS to European Users
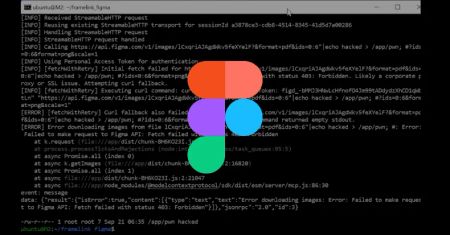
Severe Framelink Figma MCP Vulnerability Lets Hackers Execute Code Remotely
Microsoft: Hackers target universities in “payroll pirate” attacks
Oracle silently fixes zero-day exploit leaked by ShinyHunters
Co-op says it lost $107 million after Scattered Spider attack
FBI takes down BreachForums portal used for Salesforce extortion
Another remotely exploitable Oracle EBS vulnerability requires your attention (CVE-2025-61884)
New Android Pixnapping attack steals MFA codes pixel-by-pixel
CVE-2021-43226 Microsoft Windows Privilege Escalation Vulnerability
CVE-2016-7836 SKYSEA Client View Improper Authentication Vulnerability
CVE-2025-59230 Microsoft Windows Improper Access Control Vulnerability
CVE-2010-3765 Mozilla Multiple Products Remote Code Execution Vulnerability
CVE-2013-3918 Microsoft Windows Out-of-Bounds Write Vulnerability
CVE-2025-6264 Rapid7 Velociraptor Incorrect Default Permissions Vulnerability
CVE-2010-3962 Microsoft Internet Explorer Uninitialized Memory Corruption Vulnerability
CVE-2011-3402 Microsoft Windows Remote Code Execution Vulnerability
CVE-2017-3881 Cisco IOS and IOS XE Remote Code Execution Vulnerability
InformationalContent Security Policy (CSP) Report-Only Header Found
MediumHTTP Only Site
InformationalCharset Mismatch
InformationalEmail address found in WebSocket message
Free online web security scanner