Session Management Response Identified
- Risk:
Informational
- Type:
- Passive
- Summary
The given response has been identified as containing a session management token. The ‘Other Info’ field contains a set of header tokens that can be used in the Header Based Session Management Method. If the request is in a context which has a Session Management Method set to “Auto-Detect” then this rule will change the session management to use the tokens identified.
- Solution
This is an informational alert rather than a vulnerability and so there is nothing to fix.
- Other info
- header:authorization
Microsoft fixes Windows bug breaking localhost HTTP connections
North Korean Hackers Combine BeaverTail and OtterCookie into Advanced JS Malware
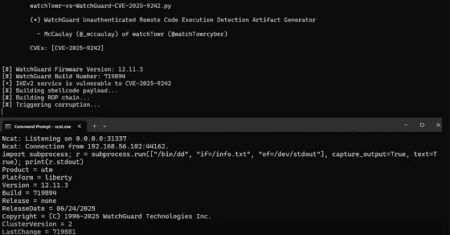
Researchers Uncover WatchGuard VPN Bug That Could Let Attackers Take Over Devices
Microsoft Revokes 200 Fraudulent Certificates Used in Rhysida Ransomware Campaign
Windows 11 updates break localhost (127.0.0.1) HTTP/2 connections
Auction giant Sotheby’s says data breach exposed financial information
Have I Been Pwned: Prosper data breach impacts 17.6 million accounts
Hackers exploit Cisco SNMP flaw to deploy rootkit on switches
CVE-2025-54253 Adobe Experience Manager Forms Code Execution Vulnerability
CVE-2016-7836 SKYSEA Client View Improper Authentication Vulnerability
CVE-2025-6264 Rapid7 Velociraptor Incorrect Default Permissions Vulnerability
CVE-2025-59230 Microsoft Windows Improper Access Control Vulnerability
CVE-2025-24990 Microsoft Windows Untrusted Pointer Dereference Vulnerability
CVE-2025-47827 IGEL OS Use of a Key Past its Expiration Date Vulnerability
CVE-2025-27915 Synacor Zimbra Collaboration Suite (ZCS) Cross-site Scripting Vulnerability
CVE-2025-61882 Oracle E-Business Suite Unspecified Vulnerability
CVE-2010-3765 Mozilla Multiple Products Remote Code Execution Vulnerability
Free online web security scanner