XenoRAT malware campaign hits multiple embassies in South Korea

A state-sponsored espionage campaign is targeting foreign embassies in South Korea to deploy XenoRAT malware from malicious GitHub repositories.
According to Trellix researchers, the campaign has been running since March and is ongoing, having launched at least 19 spearphishing attacks against high-value targets.
Although infrastructure and techniques match the pllaybook of North Korean actor Kimsuky (APT43), there are signs that better match China-based operatives, the researchers say.
Multi-stage campaign
The attacks unfolded in three phases, each with distinct email lures between early March and July.
Initial probing started in March, with the earliest email discovered targeting a Central European embassy. In May, the threat actor switched to diplomatic targeting with more complex lures.
"On May 13, 2025, an email to a Western European embassy pretended to be from a high-ranking EU delegation official about a 'Political Advisory Meeting at the EU Delegation on May 14,'" the Trellix researchers say.
Between June and July, the adversary moved to themes related to U.S.-Korea military alliance.
The targets were generally European embassies in Seoul and the themes included fake meeting invites, official letters, and event invitations, often sent from impersonated diplomats.
The lures were highly contextual and multilingual, written in Korean, English, Persian, Arabic, French, and Russian. Furthermore, to make the campaign more convincing, most emails were timed to match real events.
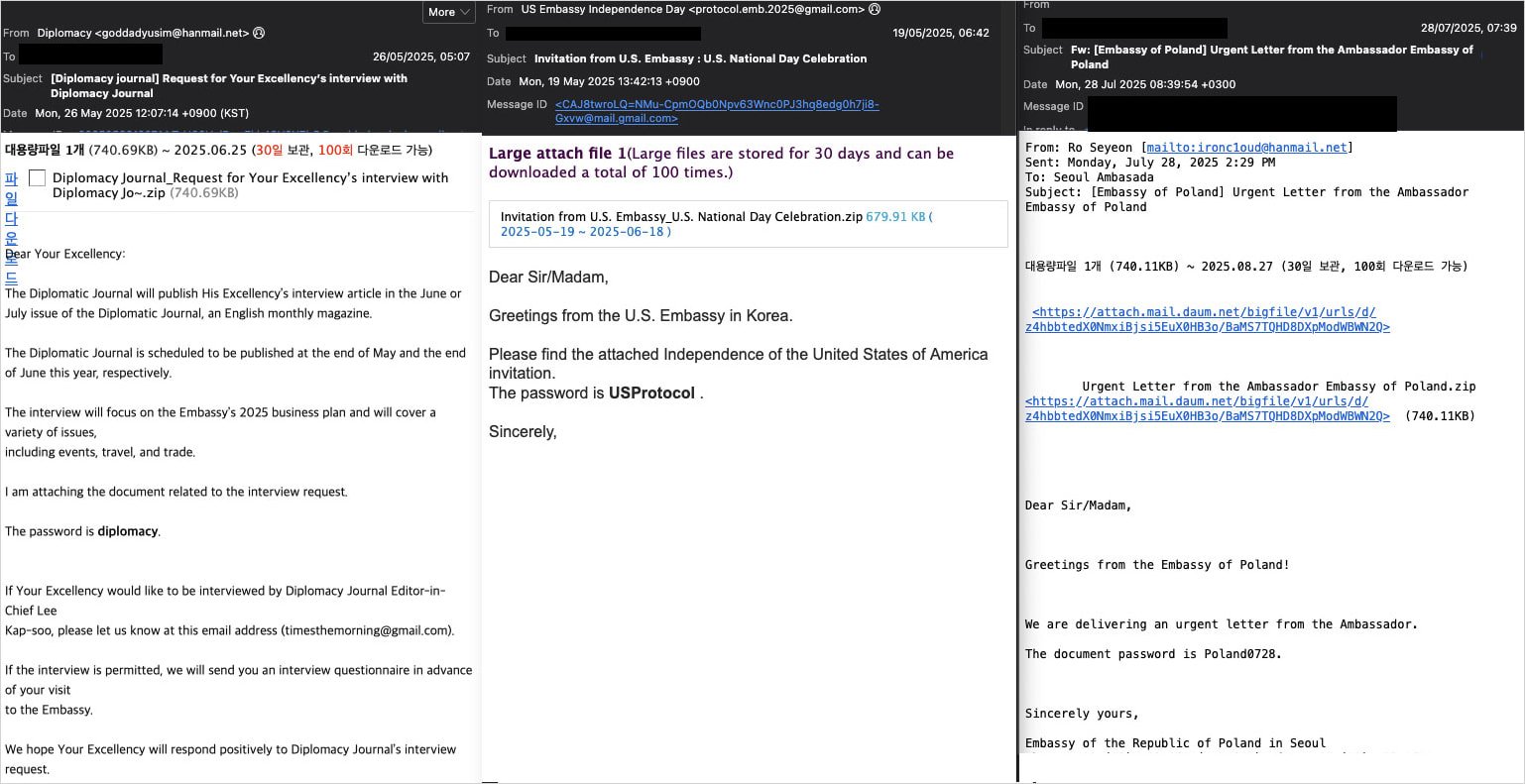
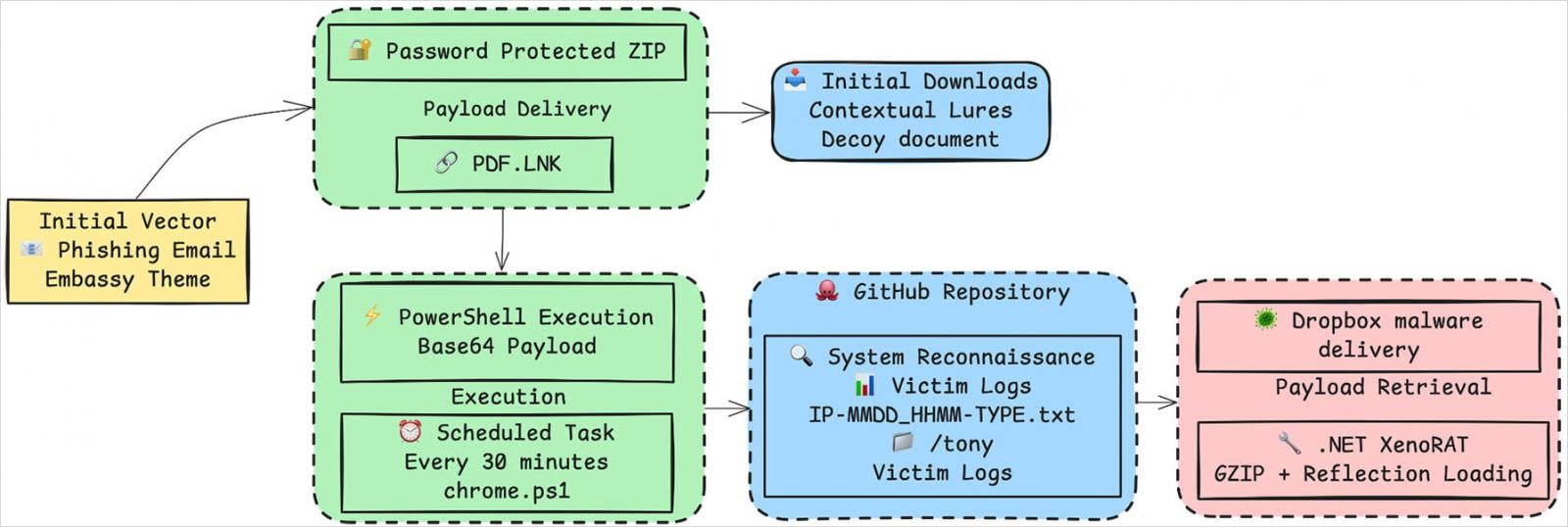
Across all phases, the delivery method remained the same, with the attacker delivering password-protected archives (.ZIP) from Dropbox, Google Drive, or Daum storage services, which would reduce the risk of email protection systems flagging the messages.
The archives contained a .LNK file disguised as a PDF. Upon launch, it triggers obfuscated PowerShell code that retrieves the XenoRAT payload from GitHub or Dropbox, securing its persistence with scheduled tasks.
XenoRAT is a powerful trojan that can log keystrokes, capture screenshots, access the webcam and microphone on infected computers, perform file transfers, and facilitate remote shell operations.
Trellix notes that XenoRAT is loaded directly in memory via reflection, and is obfuscated with Confuser Core 1.6.0, so it maintains a stealthy presence on breached systems.
China and DPRK flavors
Trellix underlines that these attacks match the profile of APT43 and make use of typical techniques associated with the North Korean threat group.
Hints supporting this conclusion include the use of Korean email services, abuse of GitHub for command and control, and use of a unique GUID and mutex consistent with other Kimsuky malware families.
Also, the researchers logged IPs and domains previously linked to Kimsuky campaigns.
However, timezone analysis shows that the majority of attacker activity matches a China-based actor, and the same is reflected on holiday pauses, following Chinese national holidays, while having no strong correlation with Korean holidays.
Trellix concludes that the campaign is attributed to APT43 with medium confidence, hypothesizing some form of Chinese sponsorship or involvement.