CISA warns of N-able N-central flaws exploited in zero-day attacks

CISA warned on Wednesday that attackers are actively exploiting two security vulnerabilities in N‑able's N-central remote monitoring and management (RMM) platform.
N-central is commonly used by managed services providers (MSPs) and IT departments to monitor, manage, and maintain client networks and devices from a centralized web-based console.
According to CISA, the two flaws can allow threat actors to gain command execution via an insecure deserialization weakness (CVE-2025-8875) and inject commands by exploiting an improper sanitization of user input vulnerability (CVE-2025-8876).
Although N-able has yet to confirm CISA's report that the security bugs are now being exploited in the wild, the company patched them in N-central 2025.3.1. It also urged admins to secure their systems before further information on the bugs is released.
"This release includes a critical security fix for CVE-2025-8875 and CVE-2025-8876. These vulnerabilities require authentication to exploit. However, there is a potential risk to the security of your N-central environment, if unpatched," N-able said in a Wednesday advisory.
"You must upgrade your on-premises N-central to 2025.3.1. (Details of the CVEs will be published three weeks after the release as per our security practices.)"
While the U.S. cybersecurity agency has not yet shared details regarding the attacks exploiting these N-central security bugs, it stated that there's no evidence that they're being used in ransomware attacks.
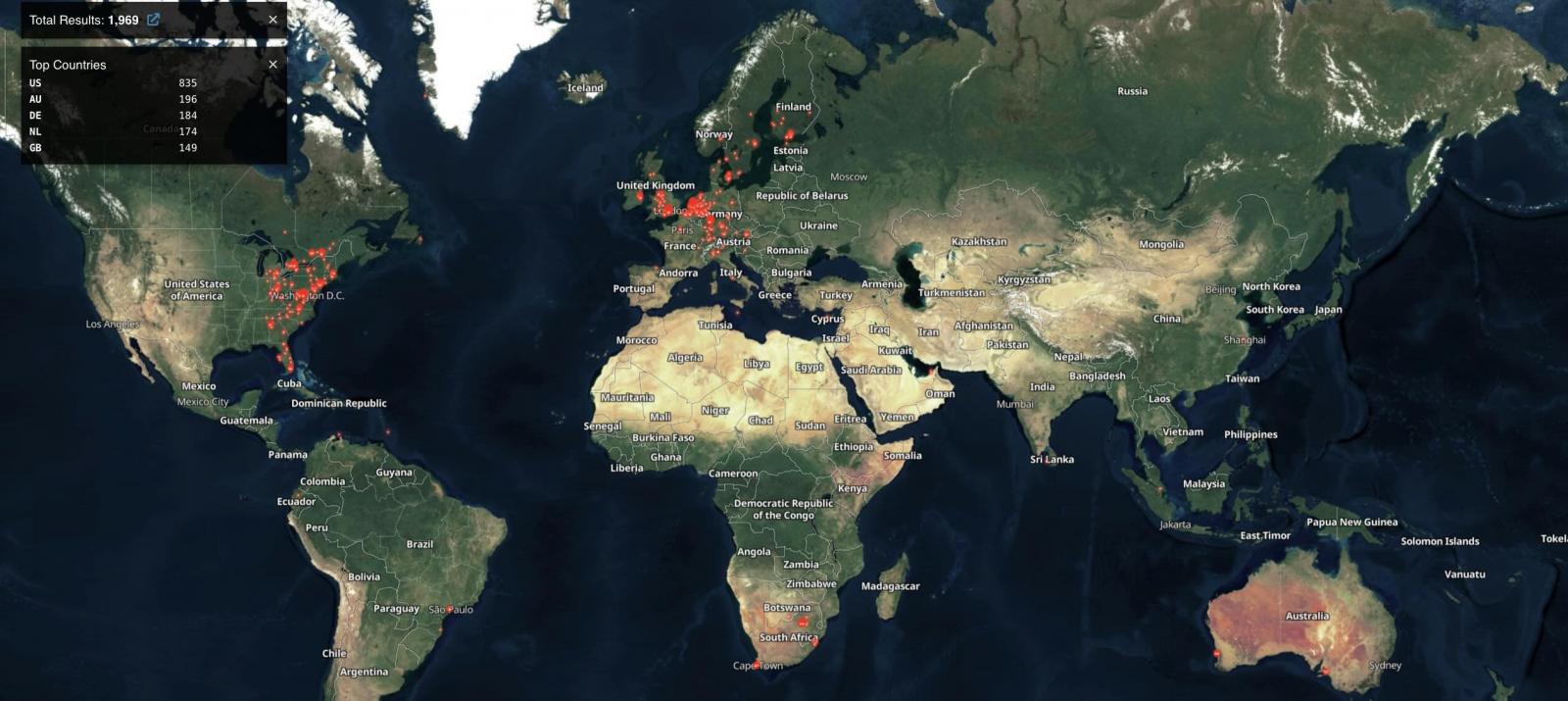
According to Shodan searches, approximately 2,000 N-able N-central instances are exposed online (some of which are likely already patched), with the majority originating from the United States, Australia, and Germany.
CISA has also added the flaws to its Known Exploited Vulnerabilities Catalog, giving Federal Civilian Executive Branch (FCEB) agencies just one week to patch their systems by August 20, as mandated by the November 2021 Binding Operational Directive (BOD) 22-01.
Even though BOD 22-01 primarily targets U.S. federal agencies, CISA encouraged all organizations, including those in the private sector, to prioritize securing their devices against this actively exploited security flaw as soon as possible.
"Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable," CISA cautioned on Monday.
"These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise."
Last week, CISA issued an emergency directive ordering non-military agencies within the U.S. executive branch to mitigate a critical Microsoft Exchange hybrid vulnerability (CVE-2025-53786) by 9:00 AM ET on Monday morning.






